Every four years, Heron Financial Group completely tears down and rebuilds its technology platform.
One big focus: A review of how every vendor handles clients’ private data, says David Edwards, head of the New York-based advisory firm.
Not all contracts are renewed.
“We’ve told vendors, 'We can’t work with you anymore because we’re not confident our data is secure,'” Edwards says. “They don’t like it, but there it is. We’re fiduciaries. That means protecting your client against every threat.”
From all sides, independent advisers are told that, to stay current, they must integrate the latest technology tools into their practice. They hear regular warnings, too, about cybertheft schemes and protecting their businesses against malicious electronic attacks.
Few advisers, however, are cautioned about the risk they face when plugging in those same tools. An exposure of client data can trigger tough regulatory action and costly lawsuits, not to mention reputational harm, even if the firm wasn’t the source of the error.
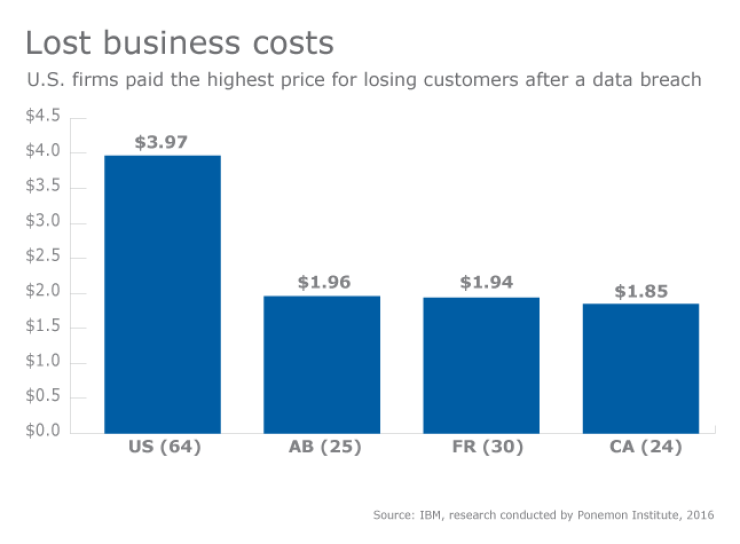
It’s not just hackers or a rogue employee RIAs have to be vigilant about. In its annual report on data breaches, Verizon deemed unintentional breaches so common that it created a category for them: miscellaneous errors. Verizon counted over 11,300 incidents last year, with almost 200 confirmed breaches. In a majority of cases, a client discovers personal data has been made public before the firm does. The financial sector suffered over 1,300 data breach incidents last year, Verizon says.

To ensure client data safety, Edwards says advisers must scrutinize contracts signed with vendors, conduct regular follow-ups, have a cybersecurity policy in place and even purchase cybersecurity insurance.
“Everything needed for identity theft is neatly packaged within your own computer systems,” Edwards says. “That’s why we go through that process of up-armoring everything we do.”
WHO’S REALLY RESPONSIBLE?
The modern RIA uses an array of tools — CRMs, form generators, portfolio management and risk-analysis applications, to name just a few — that access client data. These tools give advisers deeper insights about clients, as well as the means to run their practices more efficiently.
Though the developers of these tools are private companies competing for the same advisers, they have collaborated on building programming integrations, creating joints and fittings that are all part of a virtual data pipeline extending from an RIA’s computer and servers to those utilized by tech vendors, and ultimately to custodians and brokerages.
The data flow goes both ways. Custodians and brokerages generate trade and transaction data for RIAs that they download. It’s a system that has developed and expanded over time organically, and it works.
It’s not just hackers or a rogue employee RIAs have to be vigilant about.
But there’s a slow-burning industry debate over data ownership and the role it should play should that piping spring a leak, and client-sensitive information (account numbers and balances, Social Security numbers, birthdays) becomes exposed.
Most tech providers, custodians and brokerages state in documents and business agreements that an RIA is the owner of their clients’ data and, as the fiduciary, is responsible for safeguarding it.
Take, for example, the case of R.T. Jones Capital Equities Management of St. Louis, which, according to the SEC, suffered a data breach in July 2013 when a third-party-hosted web server it was using was hacked.
PAYING THE PRICE
Thousands of client records were exposed in the incident, which was traced back to a China-based attacker. Though the SEC noted that no client was harmed financially, the firm settled with the SEC for $75,000 in 2015 for not having a cybersecurity policy in place.
That case makes it clear that advisers, not technology providers, will be held responsible by securities regulators for a breach, says Bryan Baas, managing director of risk oversight at TD Ameritrade Institutional.
“It comes down to, ‘Who is the regulator regulating?’ ” Baas asks. “They only go after who they have authority over.
“Legally, you could argue the vendor screwed up, and that it’s not your fault. But the regulator has no authority over the vendor. You’re the fiduciary. You’re supposed to protect your clients’ information.”
‘AMORPHOUS’ LIABILITY
Advisers will find little protection in their agreements with their tech providers, notes Cary Kvitka, a securities attorney with the Lawrenceville, New Jersey-based firm Stark & Stark.

Standard industry practice among vendors is to include clauses stating that they are not liable for any data breaches that may occur.
“Every party tries to obfuscate their responsibility,” Kvitka says. “Everyone tries to waive all liability from the beginning of time to the end of time. It’s just a matter of if that holds up in court.”
The challenges presented by securing client data as its uses and volume increases should keep advisers up at night, compliance pros say.
“The liability is so amorphous,” says Chad Christensen, chief compliance officer of Semper Augustus Investments Group in Highlands Ranch, Colorado. “What do you do about it? What can you control? People sit and worry about China when, probability wise, it’s going to be something relatively simple that will become a problem. You’d better be in control of what you can control.”
Expect more litigation between RIAs and vendors.
Advisory firms will begin pushing back on bearing the responsibility and costs in the event of a breach they did not cause directly, says Lisa Marsden, president of the Miami-based compliance consulting firm Coulter Strategic Services.
According to the cybersecurity firm SecurityScorecard, 16% of firms using cloud server providers received a failing grade in terms of updating their defenses regularly against attacks. “You have a certain level of responsibility to keep your clients’ information safe,” Marsden says. “But there are different sources of sensitive client data — from the custodian, from the portfolio management software — so definitely the ownership can be shared.”
NARROW THE LIABILITY GAP
Though the idea of bearing responsibility for safeguarding client data while a vendor handles it might seem onerous, there are a number of steps that can minimize risk to clients and narrow the liability gap, too.
The first step is effective information, says Michael Delgass, CEO of New York-based Sontag Advisory.
“It doesn’t mean you have to learn how to code security software, but you have to know more about the tools that you are using, where to go for help and how to stay informed where things are changing,” Delgass says.
“For example, more people are going to work remotely. So it’s increasingly important to understand where they are pulling down data from, where that data is being stored and the measures you have to protect that data. As you allow people to do more things with technology, you have to know the threats to those areas, too,” he adds.
"The regulator has no authority over the vendor. You’re the fiduciary. You’re supposed to protect your clients’ information.”
Advisers should take inventory of all client data they share and identify who has access to it internally and externally, Marsden suggests.
That can help determine vulnerability and risk among parties, as well as pave the way for more-detailed inquiries into whom your vendors share that data with, how they transmit it and where they store it.
That effort takes time. “You can’t just pick it up on a weekend, as many advisers tend to do,” Marsden says. “You should have a process.”
NEGOTIATE, NEGOTIATE
Knowledge and structure will help firms to know their vendors better and to ask smarter questions about how client data will be handled, Delgass adds.
That’s crucial in the due diligence process, not only in vetting a vendor, but also in being able to scrutinize vendor contracts with data security in mind.
Any contract, for instance, should spell out who has the responsibility to notify affected clients in the event of a breach, Marsden says.
At his firm, Delgass says, vendors are pushed to explain in detail their data-handling procedures, including how they acquire files, what confidentiality agreements their employees sign and how they control clients’ information when they access it.
And they push back against the standard liability clauses.
“Any contract is an opportunity for negotiation,” Delgass says. “We read the clauses, and we changed them. Those are a starting point, not an ending point, if you’re doing things right.”
Marsden agrees, noting that she counsels her clients to seek added protections in their agreements with vendors, whenever possible.
“Nobody can guarantee anything 100%, and every party is going to be different,” she says. “But you should push back to get an agreement that you will at least get help if a situation occurs, especially if the circumstance comes under them.”
There are technical barriers that advisers can place around clients’ data, such as encryption, protected servers with redundancies to store information and more-secure platforms for communicating with clients, says Edwards of Heron Financial, who also sits on the advisory board of eMoney Advisor.
TOUGHER MEASURES
Having tougher measures means that advisers may have to allow for an adjustment period on the part of clients, he adds.
His firm adopted encryption for all outbound email, but had to stop because most clients could not open the correspondence.
And then there is paperwork: Every RIA should now have a cybersecurity policy, and it should have insurance against liability claims, Stark & Stark’s Kvitka says.
In September, the SEC proposed rules requiring advisory firms to have cybersecurity programs. The SEC and FINRA have increased examinations of firms’ digital controls, with a greater focus on cybersecurity.
Crucial in defending against a breach claim is being able to demonstrate that an RIA firm made the best effort possible to reasonably determine the safety of its clients’ data, Kvitka says.
“A focus will come on what did you do before you let a vendor access your data,” he says. “Advisers need to have as much information as possible, as specific as possible, to say they were confident that clients’ data was secure. The more you know, the more you can document, the safer you are.”
One source Kvitka studied for insights into developing a cybersecurity policy: the health care industry’s stringent standards for handling confidential patient information under the HIPAA law.
The need for information shouldn’t stop once a partnership has been agreed upon, warns Dan Skiles, president of the San Diego-based custodian Shareholders Service Group, and an FPA board member.
Skiles says the FPA recently quizzed members on how they work with vendors and found that many did not keep up their initial checks.
'ONE AND DONE'
“After they go through the due diligence and the agreement, they have very little work done on the follow-up, as it relates to making sure the data is safe, and checking in on a regular basis to make sure there have been no breaches,” he says. “Not even annual checkups with their vendors for their own documentation to show their clients; it’s sort of one and done.”

This lapse in discussions isn’t always a lack of effort on an adviser’s part. Often, the vendor dodges some data security questions, either by offering formulaic responses or begging off specific requests, citing proprietary concerns.
“One thing I wish I could see more from vendors is to be more understanding and willing to dedicate time to the adviser due diligence process,” notes Michelle Thetford, vice president of client strategic solutions at Schwab Advisor Services.
“It’s very common, especially among larger vendors, to not be very flexible with due diligence questions,” she adds. “Advisers are ready to spend the time, but what they get is a canned, one-page answer. Vendors don’t want to engage in a dialogue. They need to understand advisers are being held to a much higher standard. They can’t use a vendor if they aren’t confident in them.”
TD Ameritrade’s Baas acknowledges the difficulty that small RIA firms may encounter when dealing with vendors in their efforts to get more assurances about data.
He suggests those firms consider TD’s approach to integrating with vendors. “We give them our requirements for transmission of data,” he says. “If the vendor says, ‘I can’t do that,’ we will not do business with them.”
The process need not be adversarial, however.
Advisers need to understand that tech vendors are deluged with due diligence requests, says Greg Friedman, president of the CRM provider Junxure and the wealth management firm Private Ocean.
And vendors who are integrated with the biggest custodians and brokerages have already gone through rigorous testing of their data controls, he adds.
Vendors do acknowledge the challenges facing RIAs as the responsible stewards of clients’ data, says Eric Clarke, CEO of Orion Advisor Services, which develops software and adviser platforms.
Attempting to develop best practices on how to handle data, Orion and other providers are working on a proposal for a private network to communicate clients’ data more securely, Clarke says. Another proposal would reduce the amount of personal information transmitted between vendors and custodians.
EQUAL RESPONSIBILITY
As an adviser and technology provider, Friedman sees equal responsibility in making sure clients’ data is kept safe.
“Rather than get into a debate about who owns the data, I believe everyone who touches it has an ownership stake in it,” he says.
It’s a point that Heron’s Edwards is willing to concede.
Just five years ago, his six-employee firm had no budget for cybersecurity. But in the past year alone, he has spent $60,000 on cybersecurity measures.
Advisers, Edwards says, have to commit to staying on trend with best practices in technology, and they also have to commit dollars.
“You cannot hide from this,” he says. “The upside to not spending on data and cybersecurity is that you’ll save money. But the downside is that, if there’s a breach, you’ll be gone in an instant.”